The access to the system can be restricted to specific IP. This allows the system to be safe from unauthorized access from outside the campus even if the login credentials and passwords are shared.
Access can also be limited for limited time period for different levels of users. For example, the students may be allowed to access the system for all 24 hours, but the access for the administrators or staff may be limited beyond the office hours.
The system records the login time and login IP address of each member to keep a record of the activity done in the system.
Besides several checks imposed to keep the system safe from unauthorized access, there are several permissions and specific rights that restrict a user from accessing certain areas of the system and even if it allows to enter, it restricts to perform a certain task which is out of the scope of the current user profile.
The permissions are divided into three main categories, System Permissions, Member Access Permissions, Task Specific Permissions.
System General Permission can be understood with the example that if a user is given permission for User level master entry, then he may be able to add a new school to the list while adding a students form into the system, but the same user cannot add a new course which needs Admin level master entry permission to do so.
Similarly a junior employee might be allowed to draw and print reports and but not to export the data into excel or an other soft copy format. And maybe a new comer staff is not even allowed to see reports and lists generated from the system.
Member type permissions can be understood with the example that, a counsellor may be allowed to access member records only of leads/enquiries but not the information of enrolled students or staff members.
Task specific permissions can be understood as the example of a case where the placement officer is entitled to access the information of students but not the accounts module where the fee information of each enrolled student is stored. Likewise a faculty may be allowed to see the list of students of the batch in which he is teaching in order to mark their attendance or to write comments about their performance but not to see their complete address or contact details.

The Super Admin can create more admins by allocating required set of permissions necessary to fulfil the intended tasks. A set or special rights can make an admin a super Admin. So given these special rights there can be several super admins in the system. However it is suggested to have only one.
A Super Admin is the member of Head Office, who has access to the highest controls of the system like giving permissions and access rights to the other registered members to make them admins or to restrict their access to the system as limited users. A super admin can do rare tasks like creating a new branch or adding a branch admin or adding a new course applicable for several branches. A super admin has the access to take backup of the entire database and to delete or clear it.
There can be different types of Admins, Super Admin, Branch Admin, or and admin based on specific task profiles. An Admin is ideally a profile. So there can be a staff member Mr. X and he can have a staff login where he can have access to his own payslip and other details at the same time he can also act as an Head of Department of some department and can have the Admin Id with permissions and access rights of an Head of Department.
A head office user can see information of all the branches created in the system, but a branch user has access limited to records only of his branch.
This access of the head office user is however limited according to the General System, Member and task specific permissions allotted to that admin member.
A head office user can move registered members from one branch to other.
The user level entries done in a specific branch by a specific branch user are not visible to the users of only that branch. For example if there are two branches Delhi & Bombay, then if the admission clerk of Delhi Branch adds a new school to the list of schools, then there is no point of this Delhi school to be listed for the Bombay branch user. So he entry made by Delhi branch is visible only to the Delhi branch.
The Super Administrator can access a Administrator Settings Dashboard where he can make settings that will effect the general functioning of the system.
The default behaviours on various system activities are set by the administrator for example: whether list of candidates at various places to be shown in alphabetical order or in ascending order of ID or in descending order of ID can be set by altering the system settings.
Whether the Fee receipt should be acknowledged with and SMS or not can also be set as a basic system setting.
The default number of books issued to a member in library and the number of days after which the fine will be applicable etc can all be present as settings parameters of ECAS.
The above are just a few examples of System Settings in ECAS. There are hundreds such settings which lets the administrator configure his copy of software to behave in his desired way for a smooth and comfortable working experience.
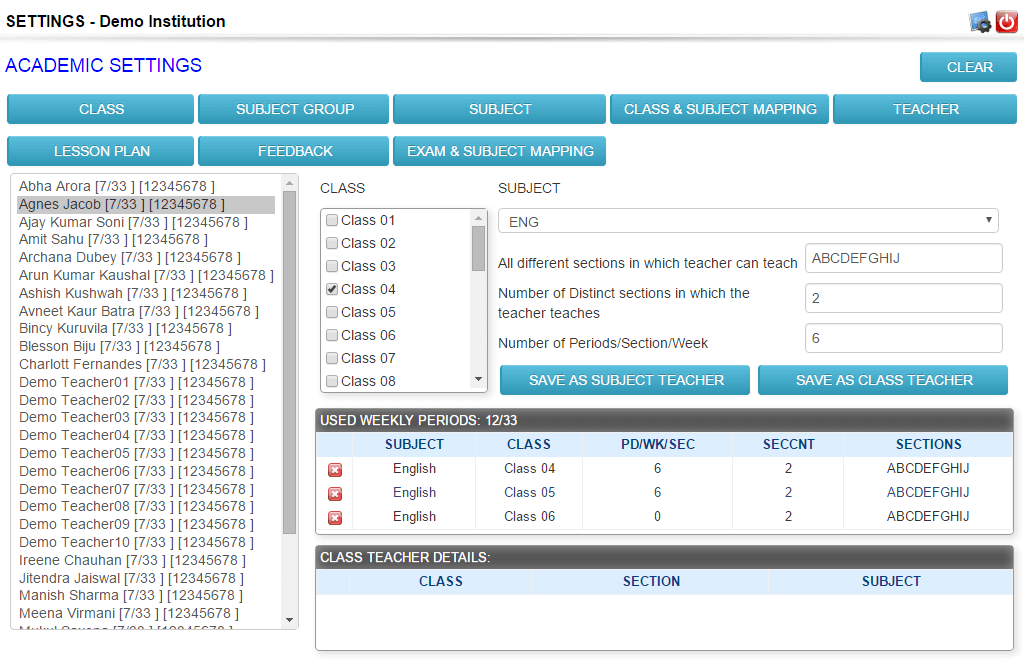
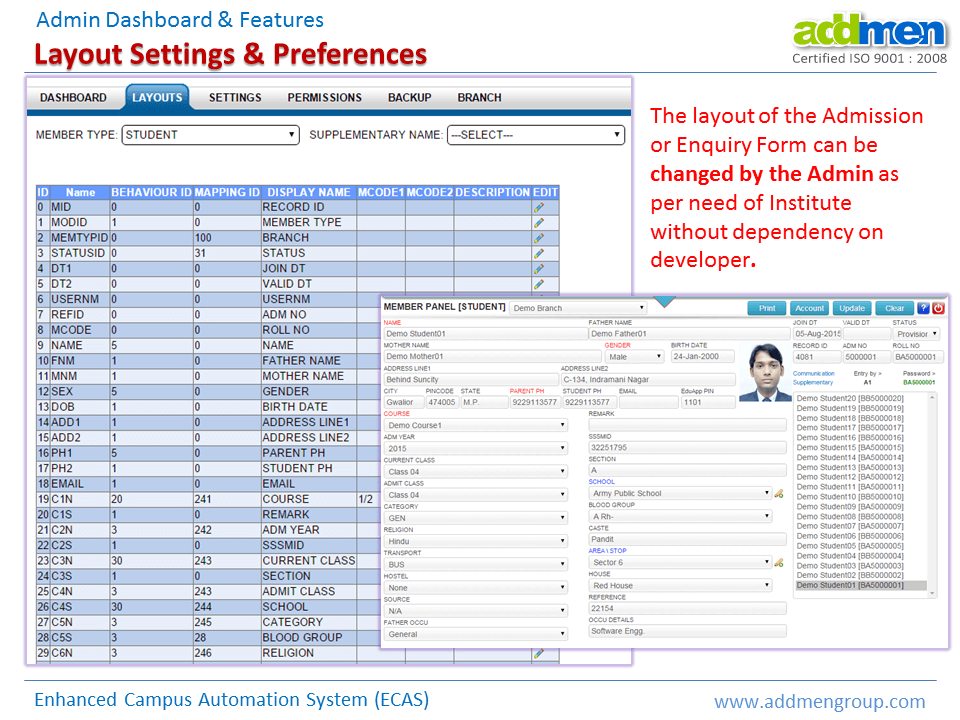
The layout of Admission forms and the behaviour of each field in the admission form can be altered by the administrator.
Addmen Group Copyright 2023. All Rights Reserved.